
Editor's note - The author of this article cites statistics from the 1990s, in the UK, since this is where he was from and the time period in which the article was written. The statistics were mentioned only to illustrate a point, so no attempt was made to update them with more current data.
The best known and most widely used type of electronic security unit is the ‘burglar’ alarm, which is designed to detect burglars attempting to break into protected premises, but lets authorized individuals roam freely within those premises, and to easily enter or leave their perimeter zones.
To be really effective, burglar alarms must be used in conjunction with various physical defenses/deterrents and with reliable locks, latches, and security windows, and their sensors and sirens must be located to give the best possible security to the individual premises that are being protected.
Note that the main goal of an anti-burglary security system is that of deterring potential burglars from even trying to break into the defended premises; the burglar alarm is simply a back-up to that system and is thus of value only if the main deterrent security system fails in its task.
To get the best value from any burglar alarm, the user must first learn the basic principles of anti-burglary protection, and must then use that knowledge to convert the basic burglar alarm into a device that gives a performance that is tailored to suit some specific security application.
This episode of our series gives a concise outline of these various principles; our next episode will show a variety of practical build-it-yourself domestic-type burglar alarm and accessory circuits.
ANTI-BURGLARY BASICS
THE BURGLAR
A burglar is a person who forcibly enters houses or other premises with the intention of theft. To be burglarized is a vile experience.
At best, the burglar may be a professional who will enter your home and steal many of your personal possessions, some of which will have a sentimental value far in excess of their insured monetary cost. The next day that same burglar will probably sell those precious goods for a trivial amount of money, and then go and rob someone else.
At worst, your burglar may be a demented amateur who enters your home with a heart full of hate, intent on stealing your cash and destroying or desecrating everything else. He will slash your furniture and clothes, urinate on your bedding, smear excrement and paint on your walls, and try to smash or burn everything else. This type of burglary is so repulsive that many victims never recover from the psychological damage caused by the experience.
Your vulnerability to burglary is greatly influenced by the location and nature of the premises in which you live or work, and by the security precautions that you take to protect those premises.
In all advanced Western countries, annual burglary totals are proportional to national population figures and are typified by those of the UK, which has a total population of about 56,000,000.
In the UK, the annual total of burglaries in the 10 years up to 1997 averaged about 900,000, of which approximately 400,000 were domestic burglaries.
Of these domestic incidents, almost three-quarters involved actual physical forced entry, and more than a quarter were walk-in burglaries in which the intruder entered the premises via an unlocked door or window or — in a small number of cases — by using a carelessly hidden spare front door key.
For security purposes, all private premises can be regarded as defensible fortresses (houses or other buildings) that are surrounded by defensible outer border zones (private land, with outer fences and hedges, etc.).
No burglar can reach your private fortress without first passing through at least one of its outer border zones, which thus form your first and most important anti-burglary defense areas. If you use these areas sensibly, you will deter most burglars from even trying to break into your house.
Figure 1 and the next two major sections of text help illustrate some of the basic defense principles of these areas, specifically applied to medium-sized houses of the types found in many suburban areas.
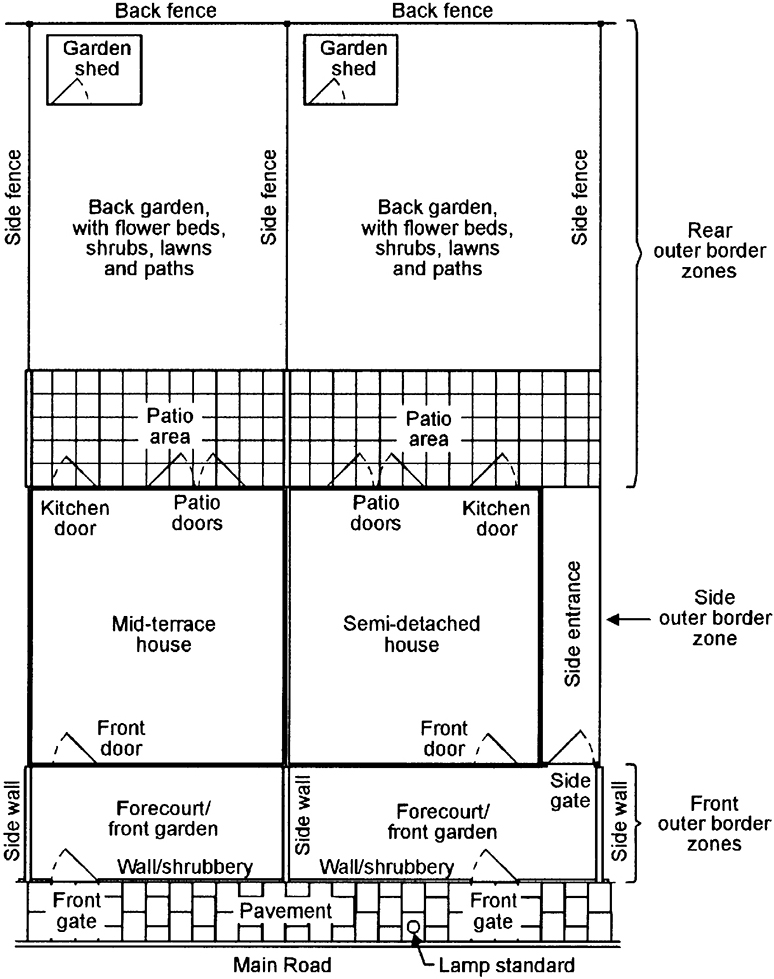
FIGURE 1. Diagram showing the outer border defense zones of typical UK-style mid-terrace and semi-detached houses (see text).
FRONT OUTER BORDER DEFENSE ZONES
Most burglars make an unobtrusive visual study of a building by walking or driving casually past it to determine whether or not it seems an easy or a not-worth-the-risk target for burglary. Their main goal is to get into and out of the premises unobtrusively so, therefore, they like houses that have their front gardens enclosed by high shrubs or bushes, or are shrouded in darkness at night, or seem to be unoccupied, or have no obvious anti-burglary protection.
Most potential burglars can be scared off by taking simple precautions such as fitting the building with time switches that automatically operate house lights at various times, or by leaving a radio switched on when the house is empty, or by fitting a real or dummy alarm bell housing to the front of the house.
If burglars decide to attack a house from the front, they usually enter the garden via the front gate and then try to enter the house by the front door or — if the house has a side entrance — by forcing the side gate and then entering the house from the rear.
Burglars know that some people hide a spare front door key in or near the porch when they leave the house, and burglars often make a quick search for such a key. You can take advantage of this fact by making a simple ‘false key’ booby trap that activates a self-latching alarm if a dummy key or some other object is briefly moved.
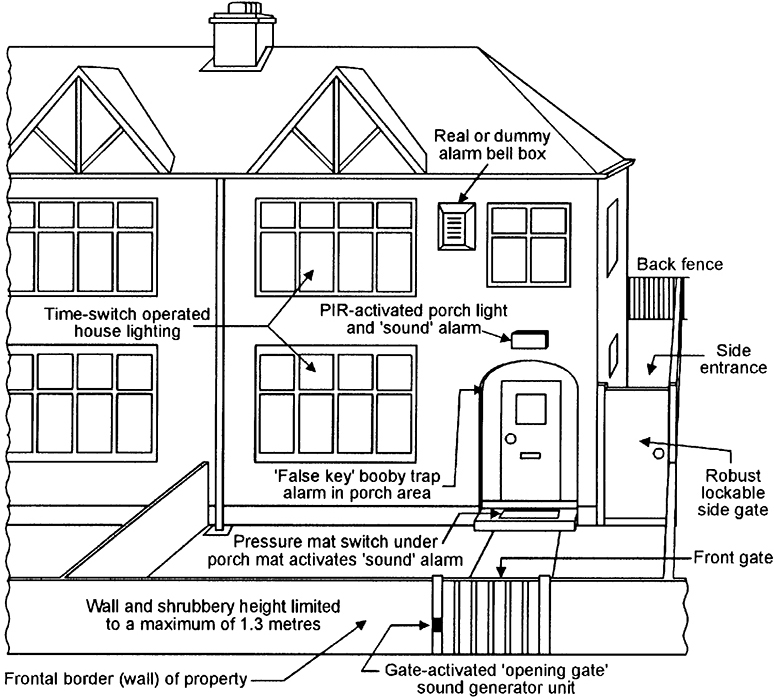
FIGURE 2. Diagram showing various burglar deterrents used in the front outer border zone of a semi-detached house.

FIGURE 3. Diagram showing basic arrangement of an IR light-beam side entrance defense system.
Thus, basic rules for protecting the house against frontal attack are as follows, and are illustrated in Figures 2 and 3:
- Limit all front garden shrubbery to a maximum height of 1.3 meters.
- If your house front is poorly lit at night, fit it with an automatic PIR-activated porch lighting system.
- If your front gate is a self-closing type, fit it with a device that generates a distinctive sound as the gate is opened.
- If your front porch is not fitted with automatic PIR-activated lighting, place a hidden pressure mat switch in the porch and use it to activate a bell or other warning device when anyone treads on it.
- Deter burglars by fitting a real or dummy alarm bell box to the front of the house, by fitting the house with time-switch operated lighting, and by leaving a radio turned on when the house is unoccupied.
- Fit a simple ‘false key’ booby trap in the porch area.
- If you have a side entrance, fit it with a robust and lockable gate at its house-front end. Fit the side entrance with some type of intrusion-detecting alarm device that will activate if any unauthorized person enters the side entrance (even if they do so by climbing the gate), but will not be activated by cats, etc.
House side entrances have a typical length of about 10 meters and are best defended by a PIR alarm fitted with a ‘corridor’ type of lens, or by an IR dual ‘light beam’ alarm of the type described in Part 5 of this series. Figure 3 shows the basic arrangement of a suitable two-beam IR light beam alarm system.
In Figure 3, the IR dual-beam transmitter (Tx) is fixed to the side gate — near its ‘fence’ edge — and is aimed diagonally along the length of the side entrance, at a height of about one meter, towards the IR receiver (Rx) unit, which is fixed to the house wall at the far end of the entrance. Thus, the beam’s Tx to Rx contact will be broken if the gate is opened, or if any adult person moves along the side entrance when the gate is closed.
REAR OUTER BORDER DEFENSE ZONES
Three-quarters of all house break-ins occur at the back of the home (where the burglar is least likely to be seen), usually via a window. To reach the house, the burglar must cross the garden and patio areas, and usually reaches these by climbing a back or side fence or via a side entrance; homes with rear access via a shared passage or driveway are very vulnerable to this type of break-in.

FIGURE 4. Diagram showing various burglar deterrents used in the rear border zone of a semi-detached house.
Once a burglar has entered one garden, he can easily gain access to adjacent houses by climbing over their side fences, sometimes breaking into several houses or their sheds or garages in a short space of time. Thus, basic rules for protecting homes against attack from the rear are as follows, and in some cases are illustrated in Figure 4:
- Burglars treat garden sheds and garages as valuable sources of tools and equipment for the break-in and for later sale, and often break into them before attacking the actual house. Thus, always fit your shed and garage with a simple battery-powered burglar alarm that activates a loud siren and a light strobe if not disabled (via a secret switch) within about 20 seconds of opening the shed/garage door.
- If you keep a ladder in the rear defense area, wire it to a simple ‘loop’ alarm, so that the alarm sounds if the ladder is forcibly moved.
- If your home has rear access via a passage or driveway, protect the top of your back fence/wall with barbed wire or in some other way.
- It is not practical to protect side fences against a burglar who wants to climb over them. Usually, however, the burglar is climbing them to reach the back of your house via the patio area, which can easily be protected via a PIR-activated flood-light/alarm unit or an IR light-beam alarm unit that is aimed along the back of the house a meter or so above ground level, as shown in Figure 4.
- If an IR light-beam is used, it must be positioned so that its beam cannot be broken by carelessly placed patio furniture or by growing shrubbery.
- Sometimes the burglar may climb your garden fences to reach an adjacent property. You can detect this type of intrusion with an IR light-beam alarm unit that is aimed along the length of the garden, between the house and the garden shed (see Figure 4).
- If your house has a shared side entrance that leads to a pair of garages, mount a cheap dummy TV camera (with a built-in flashing LED that is powered from a remote battery) in a hard-to-reach position on the apex of the garages, aiming it along the entrance so that it is clearly visible from the street, as a burglar deterrent.
FRONT-DOOR ROBBERS
The easiest way to get into someone’s house is to simply knock on the front door and, when it opens, either barge or trick your way into the premises. Small-time crooks (including small children) often use the latter technique to carry out petty robberies, typically arriving as a pair and getting into the house on a flimsy pretext such as using your phone to make an emergency call, or asking for a glass of water, etc. One of the pair then keeps you busy with idle chit-chat while the other person searches the house for loose cash and trinkets. The basic rules for protecting yourself against this type of robbery are as follows:
- Fit your front door with a security chain, and never unhook it unless you are sure it is safe to do so.
- Buy a fixed or mobile self-latching panic-button alarm, and keep your finger on its button whenever you open the front door to a stranger.
- Never allow anyone (including children) into your house unless you are absolutely sure it is safe to do so.
- Never, under any circumstances, allow two or more strangers (particularly innocent looking children) into your house at the same time.
- Never, ever, under any circumstances, leave a total stranger alone in any part of your house; if they have the impertinence to ask to be left alone (to make a ‘private’ telephone call), immediately order them to leave the house and then inform the local police.
THE HOUSE
If the would-be burglar has successfully passed through your building’s outer border defense zones, he will now start to do physical and costly damage to the actual building by trying to break into it. His chances of breaking in are reduced (but the cost of the inflicted damage is increased) if the house is fitted with strong outer doors with robust locks/latches, and with double-glazed self-locking windows.
You can greatly reduce the crook’s chances of committing a successful burglary by fitting the house (or other building) with a properly designed burglar alarm system.
Any building can, for crime prevention purposes, be regarded as a box that forms an enclosing perimeter around a number of interconnected compartments. This ‘box’ is the shell of the building, and contains walls, floors, ceilings, doors, and windows. To commit any crime within the building, the intruder must first break through this shell, which thus forms the owner’s first line of house defense.
In most houses, the most vulnerable parts of the shell are its doors and windows, but ceilings are also vulnerable (often via a trap door and loft space) in some top-floor flats and apartments, and in many commercial buildings.
Once an intruder has entered the building, he can move from one room — or compartment — to the next only along paths that are predetermined by the layout of internal doors and passages.
In moving from one compartment to the next, he must inevitably pass over or through certain spots or areas in the building, as is made clear in Figure 5, which shows the ground-floor plan of a medium-sized house, together with suitable positions for anti-burglary devices/sensors such as PIR movement detectors, pressure mat switches, and reed-and-magnet ‘contact’ switches.
Thus, if an intruder breaks into this house via the kitchen (which has its outer door protected by a reed-and-magnet contact switch), or via the downstairs cloak room (via the side window), he can only reach the rest of the house by entering the hall, which is well protected by a hidden pressure mat switch and by a PIR movement detector, which also protects the front door and most of the stairway.
The entire lounge is well protected by another PIR unit, which is aimed away from direct sunlight (a common cause of false alarms in PIR units), but will respond instantly if anyone enters the room via its main door or its patio doors.
The dining room is not individually protected, since it can only be accessed by its doorway (which is protected by the hall’s PIR unit), or via its bay window, which (if the windows are clearly visible from the street) is a very unlikely attack point.
Thus, the entire ground floor of this house is adequately protected by just two PIR units and two detector switches. The upper floor can be protected with similar simplicity.
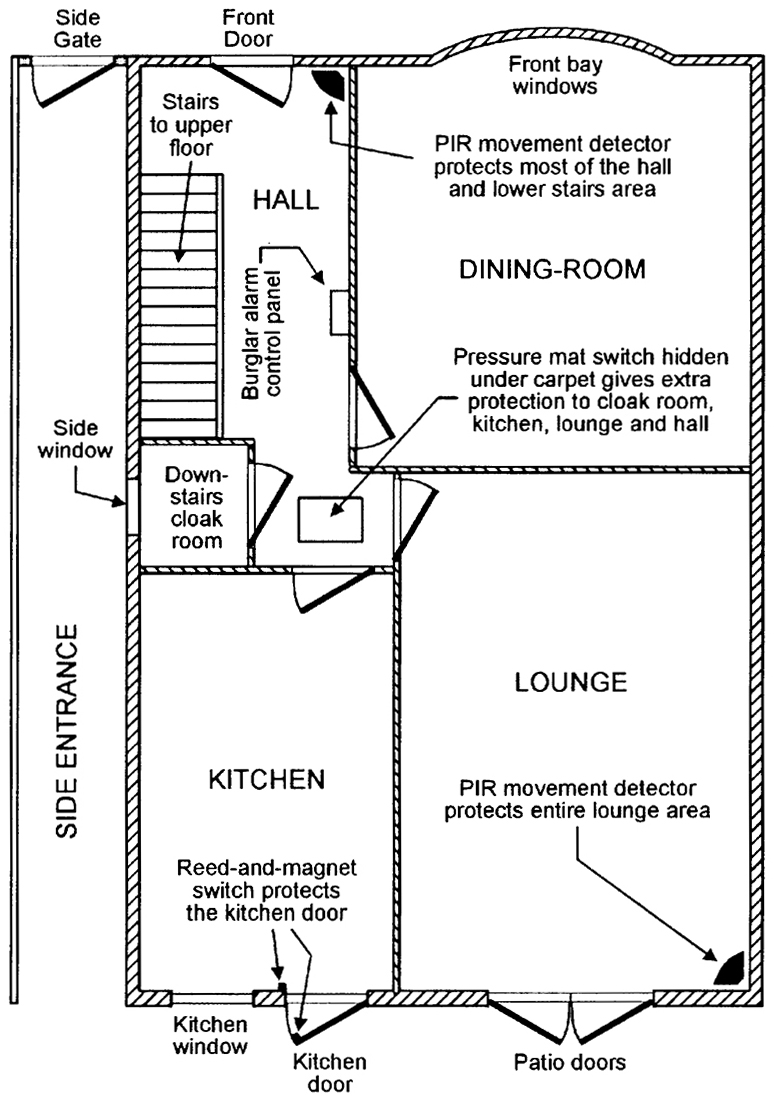
FIGURE 5. Ground floor plan of a semi-detached house, showing suitable positions for anti-burglary defenses.
Note in Figure 5 that the burglar alarm’s main control panel is situated in the hall, where it can be conveniently operated (via a security key) on entering or leaving the house, or prior to going up the stairs (to go to bed), or immediately after coming down the stairs (after getting out of bed).
The basic operating details of the burglar alarm system and its control panel are described in the next major section of this article.
BURGLAR ALARM BASICS
THE BURGLAR ALARM SYSTEM
Most modern domestic burglar alarm systems consist of a number of switched-output intrusion sensors (contact switches and PIR units, etc.) and a ‘panic’ button, which have their outputs coupled to the inputs of a master control unit that processes the received signals and — when appropriate — activates a built-in medium-power audible alarm and can — if required — also activate a high-power external siren or bell. The burglar alarm system’s block diagram thus takes the basic form shown in Figure 6.
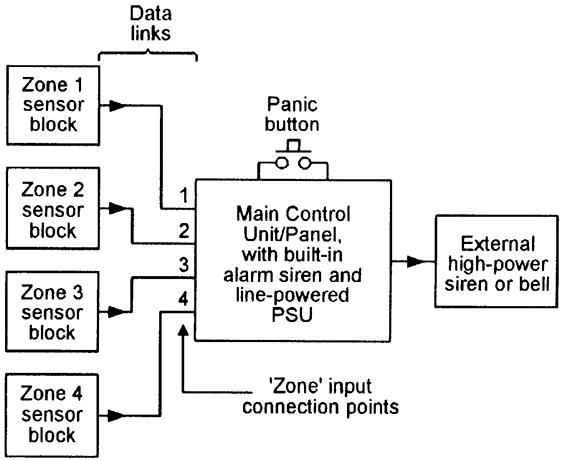
FIGURE 6. Block diagram of a basic burglar alarm system.
Note in Figure 6 that the alarm sensors are arranged in blocks or groups, each of which is allocated a specific ‘zone’ input connection point on the main control unit. The basic idea here is to divide your property into a number of distinct defense zones, each of which can cover any desired area and can have its defenses enabled or disabled via the master control unit’s control panel. Suppose that the house shown in Figures 1 to 5 is divided up into the following four defense zones:
Zone 1 = External defenses (shed, side-entrance, patio, and garden).
Zone 2 = Entire upper floor of the house.
Zone 3 = The ground floor, except the lounge and the hall pressure mat.
Zone 4 = The lounge and the hall pressure mat.
With this defense system, superb round-the-clock anti-burglary protection can be obtained by switching the zones in the following ways to suit the following circumstances:
When the house is empty, all four Zones should be enabled, thus giving total protection.
When the house is occupied during normal daylight hours, but the garden area is unused, only Zone 1 should be enabled. If only the garden and ground floor are in use, only Zone 2 should be enabled.
In the evening, if only the lounge is in use, Zones 1, 2, and 3 should all be enabled, thus protecting the occupier against the opportunist burglar who sneaks into the building while the family is watching TV in the evening. (Almost a quarter of all domestic burglaries occur when the house is occupied, with the occupiers either watching TV or asleep in bed.)
At night, when only the upper floor of the house is occupied, Zones 1, 3, and 4 should all be enabled.
Note that the ‘panic’ button is normally enabled even when all four Zones are disabled, thus giving the owner non-stop protection against thugs.
ENTRY/EXIT DELAY
In the basic type of system described above, the Zone 1, 2, and 4 defense circuitry sounds an alarm instantly if an intrusion is detected, but the Zone 3 defense circuitry (which defends the front door entry/exit and control panel areas) has built-in ‘entry/exit’ operating delays of about 45 seconds, thus giving the system’s key-holder limited freedom to pass through the Zone 3 defense area (to enter or leave the house or to operate the control panel) without sounding the alarm.
This delay action is such that, when the owner enables Zone 3 via a key switch prior to leaving the house or going to bed, the Zone does not become active until the end of the 45 second ‘exit delay’ period; when the owner later passes through Zone 3 again to deactivate the alarm via the key switch, the Zone’s sensors instantly detect the intrusion and activates a low-level ‘warning’ beeper, but only activates the main siren if the owner fails to reset the alarm (via the key switch) by the end of the 45 second ‘entry’ delay period.
Thus, the entry/exit delay facility gives the key holder reasonable freedom to move about the house without activating the main siren, but gives full protection against unwanted intruders who do not have a suitable key.
THE MAIN CONTROL UNIT/PANEL
The main control unit is the effective ‘heart’ of the burglar alarm system, and can be managed via a control panel. In simple units, the panel enables the unit’s main functions to be selected via a four-way master key switch (usually marked TEST, OFF, ON, and RESET).
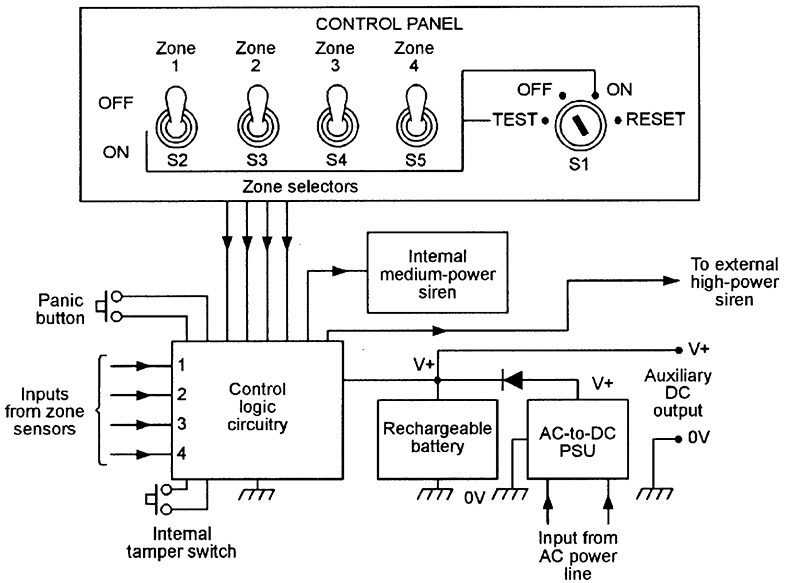
FIGURE 7. Typical basic form of a modern burglar alarm control unit and its control panel.
Most modern control units take the basic form shown in Figure 7 and are powered from the domestic AC power lines via a built-in DC PSU that also provides an auxiliary DC power output.
The control unit should ideally also have a built-in rechargeable battery that is normally trickle-charged by the PSU, but takes over the PSU’s main functions if the AC supply fails or is deliberately interrupted.
Modern control units usually have a built-in medium-power siren, plus a facility for activating a high-power external siren; ideally, the external siren should (to minimize the chances of generating publicly annoying false alarms) not activate until at least 30 seconds after the built-in siren has activated, and must (to conform to local noise control regulations) turn off automatically after a maximum period of about 15 minutes. Most units also have a built-in ‘tamper’ switch that (except when the master key is set to the TEST or RESET positions) activates the built-in self-latching siren if the unit’s case is opened.
The unit’s control panel usually takes the basic form shown in Figure 7 but, in practice, often uses electronic keypad (rather than electro-mechanical) control switching.
In this diagram, key-operated switch S1 selects the unit’s main functions, and toggle switches S2 to S5 allow individual defense zones to be enabled or disabled.
When S1 is set to the TEST position, the unit’s tamper switch and the external alarm are disabled, and the internal alarm operates in the non-latching mode.
When S1 is set to the ON position, the system is fully active and the internal alarm operates in the self-latching mode.
When S1 is set to OFF, all four sensor zones are disabled, but the self-latching PANIC facility is fully active. If the alarm is activated in the self-latching mode, the alarm can only be turned off by first removing the cause of activation and then unlatching the alarm by moving S1 to the RESET position.
In traditional hard-wired alarm systems, the sensors that connect to the alarm’s various ‘zone’ input points usually take the effective forms of contact switches, which can easily be enabled or disabled by the S2 to S5 toggle switches shown in Figure 7.

FIGURE 8. Method of enabling and disabling sensors switches via S2; (a) series-connected, n.c., (b) parallel-connected, n.o.
Figure 8 shows the connections for turning individual sections of the alarm sensor network on or off. Series-connected n.c. sensor networks can be enabled or disabled by wiring them in parallel with S2, as shown in Figure 8(a); the sensors are enabled when S2 is open, and are disabled when S2 is closed.
Parallel-connected n.o. sensor networks can be enabled and disabled by wiring them in series with S2, as shown in Figure 8(b); the sensors are enabled when S1 is closed, and are disabled when S1 is open.
THE EXTERNAL SIREN/ALARM
The medium-power siren built into most modern control units usually drives an efficient piezo-electric output transducer and operates at a fairly high audio frequency (typically 1.5KHz to 4KHz); this type of siren floods the house with sound, but such sound attenuates rapidly with distance.
Sirens designed for external use normally use an efficient horn-type loudspeaker as their output transducer and typically operate in the 800Hz to 1.2KHz audio range, which offers good long-distance acoustic coverage.
Both types of siren normally generate an attention-grabbing multi-tone (pulsed, warbled, or swept) sound, rather than a tiresome monotone sound.
External sirens are usually enclosed in a weather-proof bell-type alarm box that is screwed to the house front. The box often incorporates a flashing alarm beacon that activates at the same time as the siren. Low-cost units of this type are usually powered via a multi-cored cable, from the auxiliary power output terminals of the main control unit, and can be disabled by simply severing the power cable, which must thus be protected by burying it in brickwork, etc.
High-quality external siren units, on the other hand, are self-powered and tamper-proof, and should (to conform to current design standards) meet the following basic design specifications:
- The siren must be powered by an internal rechargeable battery that is automatically trickle charged in some way and has enough capacity to provide at least four hours of continuous alarm operation.
- The unit must be designed so that the alarm is not triggered by a temporary failure in the trickle charging system, but will trigger if activated by the main control unit, or if the unit’s main feed cable is cut.
- The box must incorporate tamper switches that automatically activate the alarm if the box’s cover is removed, or if the complete unit is forcibly removed from its fixing point (the wall).
- The unit must incorporate a timing mechanism that automatically resets the siren (but not necessarily the beacon) after (typically) not more that 15 minutes of continuous operation.
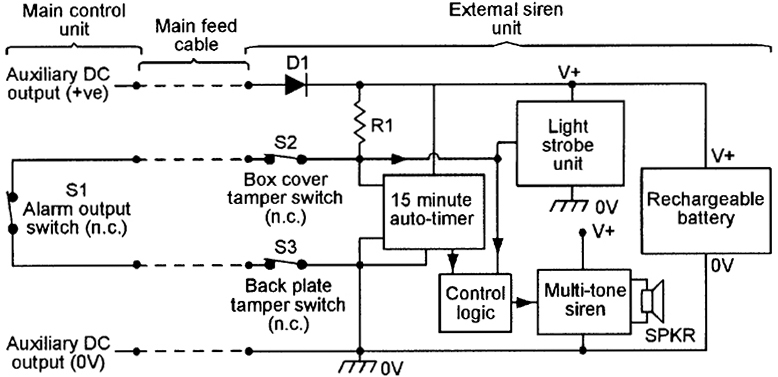
FIGURE 9. Block diagram of a high-quality external siren unit.
Figure 9 shows the block diagram of a high-quality external siren unit that is powered by a built-in battery that is trickle charged via the control unit’s auxiliary DC output terminals. This system is designed so that the control unit’s ‘alarm’ output is connected to the siren unit’s input via n.c. switch S1, which is loop-wired in series with the siren unit’s two built-in n.c. tamper switches.
One of these (S2) is connected to the unit’s box cover and opens if the cover is removed; the other (S3) is connected to the unit’s back plate and opens if the unit is pulled away from the wall. Thus, the siren activates if S1 opens, or if the main feed cable is cut, or if the box cover is removed, or if the unit’s back plate is torn from the wall.
If any of these conditions occur, the unit’s built-in light strobe activates for the duration of the o.c. condition (or until the battery is exhausted), but the multi-tone siren (which is controlled by a 15-minute auto-timer and control logic) activates as soon as the o.c. condition occurs but resets again when the o.c. condition ends or — if the o.c. condition persists — after a maximum of 15 minutes.
WIRED VERSUS WIRELESS ALARM SYSTEMS
Modern commercial burglar alarm systems are usually microcontroller based, use a keypad type of control panel, and incorporate an event recorder that — if a break-in occurs — records the precise order in which the various defense zones are invaded. Such systems come in two basic types, being either ‘wired’ or ‘wireless’ systems.
In wired systems, all zone sensors (PIR movement detectors, contact switches, etc.) are cable wired to the main control unit which, in turn, is wired to the external siren unit. Such units are time consuming and (since they use lots of interconnection cable) messy to install.
In wireless systems, all major zone sensors incorporate a wireless Tx unit that communicates (via a coded 418MHz or 458MHz RF signal) with a matching wireless Rx unit that is built into the main control unit; the Tx unit signals to the Rx unit if an alarm, tamper, or low-battery condition occurs. Such systems are very easy and clean to install, but are considerably more expensive that normal wired systems.
All domestic wireless systems are provided with a key-fob style Tx unit that can be used to remotely set or unset the main alarm unit and to act as a ‘panic’ switch that can remotely activate the alarm siren at any time. Sensor units such as contact and PIR transmitters are battery powered (usually by a PP3 type battery) and — in approved designs — give at least six months of continuous operation per battery charge.
Such units are permanently active, can transmit pre-settable identification codes, have a built-in tamper switch that initiates a full alarm condition if the unit is illegally opened, have a low-voltage detector that warns of a failing battery condition, and incorporate sophisticated energy-saving circuitry that greatly extends battery life.
PIR units, for example, transmit a brief alarm signal as soon as an intrusion is detected, but then automatically go into a (typically) 60 second shut-down mode before becoming active again. This technique conserves power when a defended area is in normal ‘zone off’ use, but gives an instant intrusion warning if the zone is alarm-active.
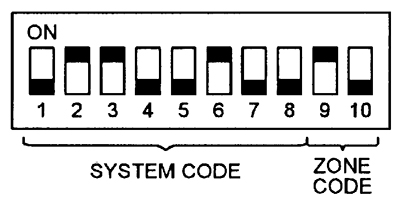
FIGURE 10. Block of 10 miniature switches built into each wireless sensor used in a low-cost wireless burglar alarm, to match the sensor’s Tx ‘system’ and ‘zone’ coding to that used in the control unit’s wireless Rx section.
Domestic-type wireless alarm systems vary greatly in price and performance. The cheaper systems usually provide a total of 256 possible identification codes and only four sensor defense zones, to which the sensors can be individually matched by a built-in block of 10 miniature switches arranged as shown in Figure 10.
Here, switches 1 to 8 enable the sensor unit’s eight-bit Tx ‘system’ code to be matched to that used by the system’s RX unit (which can be pre-set by the owner), and switches 9 and 10 are used to allocate a two-bit ‘zone’ number to the sensor.
At the other end of the price scale, some systems offer 10- or 12-bit identification codes, and up to 16 defense zones (identified by a four-bit ‘zone’ code).
Note that, in wireless systems, the main control unit identifies individual sensors purely by their zone codes. Thus, if a sensor in (say) Zone 3 transmits a low-battery-voltage warning, the unit’s control panel will display the fact. If only one sensor carries the Zone 3 code, the owner can quickly identify this particular unit and change its battery, but if several sensors carry the same code, the fault can only by traced by individually testing all of the Zone 3 sensor batteries.
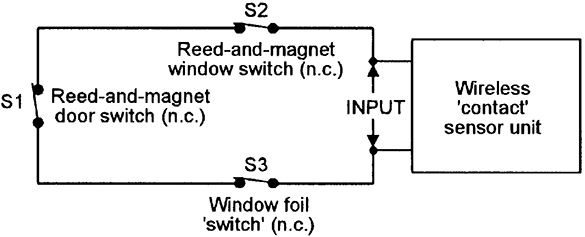
FIGURE 11. Example of three n.c. sensor switches loop-wired to the input of a single wireless ‘contact’ sensor unit.
Also note that wireless ‘contact’ sensors usually activate only when an n.c. input switch opens for a period of at least 200mS (this technique minimizing the chances of false alarming due to transient switching or signal pick-up); such sensors can be used with any desired number of n.c. sensor switches (reed-and-magnet switches, window foil, etc.) that are loop wired in the basic manner shown in Figure 11. They cannot be directly used with pressure mat switches, which are n.o. devices.
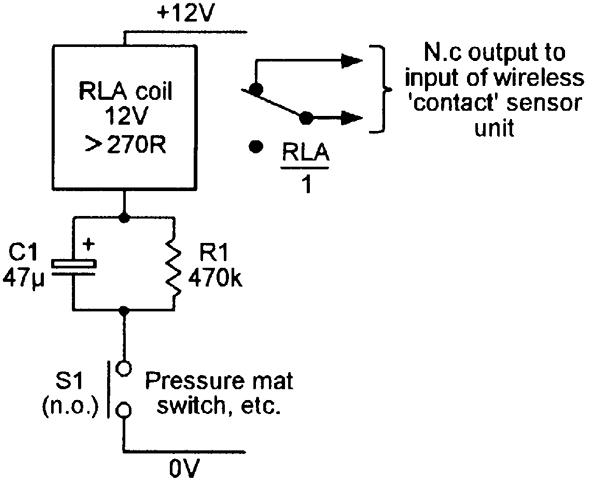
FIGURE 12. Simple adaptor circuit can be used to activate a wireless contact sensor unit via an n.o. switch such as a pressure mat type.
Figure 12 shows a simple relay-based adaptor circuit that can be used to activate a wireless contact sensor unit via a pressure mat switch or any other n.o. type of switch (or by any desired number of parallel-connected n.o. switches).
Here, 12V relay RLA has a coil resistance of at least 270R, and has one set of change-over (c.o.) contacts that have their n.c. pins wired to the input of the wireless sensor unit.
RLA’s coil is wired in series with the 12V supply via mat switch S1 and the parallel C1-R1 combination. Normally, S1 is open, C1 is fully discharged, and the RLA/1 output contacts are closed.
If S1 now closes, a heavy pulse of current flows through RLA coil via C1 and S1, thus opening the RLA/1 output contact and activating the wireless contact sensor unit. If S1 remains closed, the RLA current rapidly decays to a very low value (determined by R1) and (after a few hundred milliseconds) the RLA/1 contacts re-open. When S1 opens again, C1 slowly discharges via R1 until — after a delay of a minute or so — the system can again be reactivated by closing S1. This circuit thus draws zero quiescent current, and draws only a few microamps of mean current if S1 is closed for long periods.
Our next installment in this series will describe some wireless alarm system categories and various types of intrusion sensors, and will present a variety of hard-wired build-it-yourself burglar alarm circuits. NV














